Table of Contents
Mandatory Access Control (MAC)
The Bell and La Padula Model, often called Mandatory Access Control, describes access by active entities, called subjects, to passive entities, called objects. One entity can, depending on type of access, be in both roles.
From the distinction between read and write access four modes of access can be distinguished:
- neither read nor write (execute, e)
- read only (read, r)
- write only (append, a)
- read-write (write, w)
The set of all access types is named A.
System States
Each current access of a subject Si to an object Oj in mode x is treated as a triple (Si, Oj, x). All these triples together form the set of current accesses b.
Objects are structured according to the Father-Son-Principle and build a hierarchy H of one or more hierarchically ordered, independent trees.
All authorized accesses of all subjects to all objects are held in the matrix M. Each cell Mi,j of M thus contains a subset of A with authorized accesses of Si to Oj.
A security level is a pair (Security Classification, Set of Categories). A security classification is a value out of a hierarchy, e.g. public, confidential, secret, top secret. A category is a formal assignment to a work area.
One entity with security level (S1,C1) dominates another entity with (S2,C2), if S1>=S2 and C1 is a superset of C2. The property dominates over all entities builds a partial order D.
The assignment of security levels to subjects and objects, the classification function F, is a triple (fS, fO, fC) of security level assignment functions. fS(Si) is the maximum security level of subject Si, fO(Oj) the security level of object Oj and fC(Si) the current security level of subject Si. Thus for subjects maximum and current security level are distinguished.
For all Si fS(Si) must always dominate fC(Si).
A state z of the model is a tuple (b, M, F, H). A system is a sequence of (request, decision, next state) with initial state z0.
Security Properties
The first property to be maintained is the simple security property (no read-up). This property states that a subject Si may have read access to an object Oj ((Si,Oj,r) or (Si,Oj,w) is a current access), if Si dominates Oj.
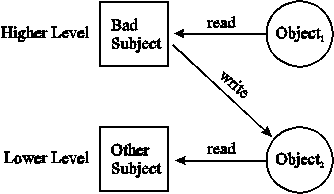 Figure 1: Illegal information flow in Bell-La Padula model.
Figure 1: Illegal information flow in Bell-La Padula model.
To prevent copying of an object to a lower security level by a malicious subject, the *-property (no-write-down) must be maintained. This property states: If a subject Si has current read access to an object O1 and current write access to an object O2, then O1 must be dominated by O2 (O1 has a lower security level than O2). Thus information flow is restricted to upwards.
As a strict accordance to the *-property would significantly reduce the usability of the system, some subjects can be marked as trusted subjects without *-property restriction.
Access control by the matrix M of authorized accesses by subjects to objects is called discretionary access control, its security property is called ds-property. The current access must always be in the set of authorized access in its matrix cell.
All properties and security levels must be mandatorily enforced by the system. Every property is added to the other ones and can never reduce system security. A state that fulfils all properties is called secure.
Decision Rules
The three properties lead to the following rules for access control decisions:
A current access (Si,Oj,x) is only granted, if the following conditions are met:
- ss-property: Si dominates Oj, if x = r or x = w (x contains read access).
- *-property: Si is trusted or
- Oj dominates current level of Si, if mode = a
- level of Oj is equal to current level of Si, if mode = w
- current level of Si dominates level of Oj, if mode = r
- ds-property: x is in cell Mi,j of matrix M of authorized accesses
Functions
To use the defined security system state transition functions are necessary. These functions must provably change a secure state to another secure state, according to the decision rules. So induction can be used to proof every reachable state to be secure.
A complete set of those functions can be as follows:
- Change set b of current accesses:
- get-access(): add triple to set b
- release-access(): remove triple from b
- Change matrix M of authorized accesses:
- give-access-permission(): add access mode to a cell of M
- rescind-access-permission(): remove access mode from a cell of M
- Change classification function F:
- change-object-level()
- change-current-level()
- Change object hierarchy H:
- create-object(): create leaf object
- delete-object-group(): remove object with all subobjects from tree
Evaluation
The Bell-La Padula model only treats confidentiality aspects. Integrity, availability and privacy of data are not protected. E.g., a subject on lowest security level can delete all data in all its categories, if it is not discretionally protected. Attacks like this can also happen without the user's knowledge, just think of malware or mistakes. Especially discretionary access control is liable to be attacked by malware.
The concept of trusted subjects which can only be implemented as users or user processes leads to further possibilities of attack by use of high level user accounts.
This model should only be used without additional protection, if confidentiality is the only issue or if data can be easily restored.
Unix System V/MLS
The model of mandatory access control used in RSBAC is mostly the same as in Unix System V/MLS, Version 1.2.1. This operating system was developed in 1989 by the National Computer Security Center of the USA with classification B1/TCSEC.
Unix System V/MLS implements the Bell-La Padula model with some smaller changes, e.g. the ds-property is replaced by Unix style access control. Security levels with classification categories are maintained, simple-security-property and *-property are enforced. In contrary to Bell-La Padula writing is only permitted on the same level.
Bell-La Padula defined four modes of access:
- execute, E
- read, R
- write, W
- Append, A
This Unix system adds ten more modes, which mostly cover parts of the above modes:
- search in directory, S
- overwrite, O
- create, C
- link, L
- unlink (delete), U
- read file/i-node status, St
- change status, Ch
- send signal/kill, K
- read IPC, Ripc
- write IPC, Wipc
Subjects are processes, which inherit their owner's security level. Four types of objects are defined:
- File
- Directory
- Interprocess Communication Channel (IPC-Channel)
- System Control Data (SCD)
Request Condition for access
- R/S/E S >= O
- W(O/A) S = O
- C/L/U S = Od
- St S >= O
- Ch S = O
- Ripc S >= O
- Wipc S = O
- K S = O
Figure 2: Access Control Conditions in System V/MLS
Figure 2 shows a summary of access control conditions. S means subject, O object, Od directory object and >= and = stand for dominates and has same level. Read and write on directories mean access to entries, open is not possible.
The RSBAC MAC implementation
Note: The RSBAC MAC module has mostly been reimplemented for v1.2.2, but this document has not yet been updated to reflect the important changes!
The Unix System V/MLS model has been changed to fit into the RSBAC access request scheme, which knows more than 30 types of access. Also, write-up is implemented in the original way, so that you can always write to all higher levels. From version 1.1.1 onwards, writing is only allowed on the same level.
Since administration depends on the role security officer, role based functions had to be added. These restrict all changes to the classification of subjects and objects and role assignments (setting of MAC attributes) to security officers.
The security_level attributes used in RSBAC are what is usually called security classifications. Categories are limited to a number of 64 for efficiency reasons. the number of security_levels is 253 (0-252, 8 Bit minus 3 special values).
The current security level (classification) and the current category set of a process are automagically adjusted as needed, if the mac_auto flag is on, which is the default value. However, mac_auto is turned off as soon as the process actively sets its current level or category set.
*-property enforcement is done with upper and lower bounds, called min_write and max_read. These values are reset only on execution of another program, not at process forking/cloning time or closing of files, because only new execution empties the process memory space.
This can lead to very limited access. Note that on write accesses, the once-only write accesses CREATE and DELETE do not adjust the min_write boundary, while MOUNT, APPEND_OPEN, READ_WRITE_OPEN, WRITE_OPEN and TRACE do.
Devices are treated similar to files with security levels and categories, and all properties are enforced. However, these checks can be turned off (attribute mac_check), because the system might become unusable otherwise.
The MAC file/dir attributes security_level and mac_categories can be inherited from the parent dir. For the security level the value to indicate inheritance from parent is 5 (4 is used internally), for categories it is the empty set (all bits 0). There are now 254 and 253 security_level special values.
RSBAC MAC-Light
Stanislav Ievlev and Amon Ott added a MAC option called MAC-Light to make the MAC module easier to use. Changes are:
- File/Dir/Fifo object creation is always granted
- Every user may mount, if levels are sufficient (used to be limited to system administrators)
When to use this model
The MAC model should be used, if you need a conceptually proven model for confidentiality. However, it is quite difficult to use in a typical Linux environment.
Table of Contents: RSBAC Handbook
Back: Security Models