Releases
Releases
Current version
Git/Latestdiff: 1.5.6
Latest Snapshots
Produced after each commit or rebase to new upstream version
GIT
RSBAC source code, can be unstable sometimes
 Events
Events
No events planned
Architecture and Implementation
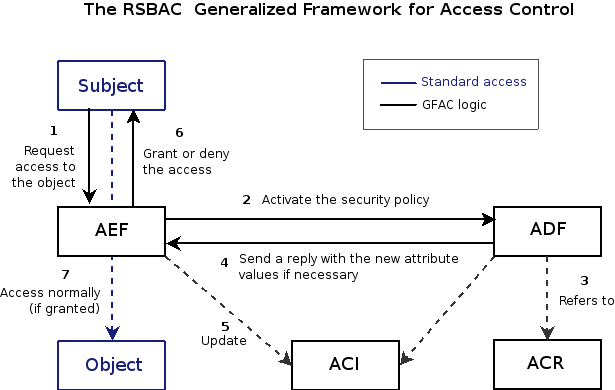
The RSBAC system architecture has been derived and extended from the Generalized Framework for Access Control (GFAC).
In his essay Rule Set Modeling of a Trusted Computer System, Leonard LaPadula describes how this Generalized Framework for Access Control (GFAC) approach could be implemented in the Unix System V operating system. He introduced the clear separation between Access Enforcement Facility (AEF), Access Decision Facility (ADF) with Access Control Rules (ACR) and Access Control Information (ACI).
The AEF, as part of the system call function calls the ADF, which uses ACI and the rules to return a decision and a set of new ACI attribute values. The decision is then enforced by the AEF, which also sets the new attribute values and, in case of allowed access, provides object access to the subject.
This structure requires all security relevant system calls to be extended by AEF interception, and it needs a well defined interface between AEF and ADF. For better modeling, a set of request types was used, in which all system call functionalities were to be expressed. The general structure of the GFAC has also been included in the ISO standard 10181-3 Security frameworks for open systems: Access control framework and into the OpenGroup standard Authorization (AZN) API.
The first RSBAC prototype followed La Padula's suggestions and implemented some access control policies briefly described there, namely MAC, FC and SIM, as well as the Privacy Model by Simone Fischer-Hübner.
Many aspects of the system have changed a lot since then, e.g. the current framework supports more object types, includes generic list management and network access control, contains several additional security models and supports runtime registration of decision modules and system calls for their administration.
Table of Contents: RSBAC Handbook
Previous chapter: Introduction to RSBAC
Next: Subjects and Objects